The inconvenient facts about Cyber
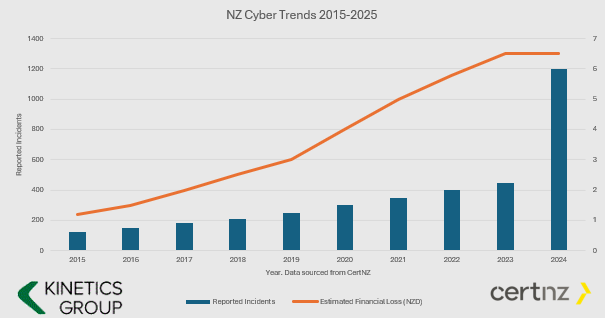
- The number and value of incidents is increasing.
- Cyber Crime is BIG business and they keep investing in new tools.
- If you aren’t keeping your defences up, then it is only a matter of time before you fall victim (i.e. if your cyber protection is the same now as it was even just one year ago, then you are increasingly vulnerable.
- You have to ward them off every hour of every day, they only have to get through once.
You might say this is scare-mongering. If all this hacking is going on and nothing has happened yet, then surely I don’t need to worry?
We’d say “good luck to you – why do you have seat belts in your car? – its only a question of time.”

What base level of Cyber Protection is Right for Me?
What base level of Cyber Protection is Right for Me?
Q: Does this mean I don’t need cyber-insurance? A: You still need cyber-insurance. We can only reduce your risk (and most insurers will want to see these protections in place before they will offer cover)
Q: What is involved installing KARE? A: Once a PC, Mac, Tablet or Phone is ready, our scripts run every time you login and the security tools auto-install – with configuration for corporate devices and BYOD.
AD HOC
STRUCTURED LAYERS based on the CertNZ Critical Controls Framework
For organisations in the cloud with minimal reliance on IT
Everything is in the cloud. There are only a few PCs/Macs and iPhones/Androids to protect
For organisations in the cloud, and maybe a small number of servers, looking to be more thorough
Add in depth reporting, server backup and identity monitoring
Pick KARE FOUNDATION SME
For organisations who value a structured, proactive IT engagement
Add more scrutiny and awareness, personalised cyber training and business planning
For organisations in the cloud with minimal reliance on IT
Everything is in the cloud. There are only a few PCs/Macs and iPhones/Androids to protect
For organisations in the cloud, and maybe a small number of servers, looking to be more thorough
Add in depth reporting, server backup and identity monitoring
Pick KARE FOUNDATION SME
For organisations who value a structured, proactive IT engagement
Add more scrutiny and awareness, personalised cyber training and business planning

What about my specific needs?
+ Choose additional services as required
Add Fixed Monthly Support Fee
No cost surprises. One fee for all business-hours support
(excludes projects and training)
Add Security Plus
24/7 SOC
IT Assets locked
Only protected devices can access them
Add Managed Firewall
Network firewall
Kinetics supplies and manages on a monthly contract
Add Password Vault
Organisation Wide
Maintain unique, complex passwords for all users and/or shared with teams
Add 365 Cloud Backup
Content backup for 365
Go over and beyond the standard Microsoft backup protection
Backup and Continuity
A range from backup to stand-by services
Because you have servers, you need to back them up

How about the broader cyber-framework?
How about the broader cyber-framework?
Platform Security is just part of a broader cyber-security and data protection framework.
Have you considered how manage your data within your Microsoft tenancy? How’s your Microsoft “Secure Score“? As you get the external security set up, let us work with you to manage the other side – your internal security.
Our consultants can work with you to understand what data your organisation maintains, and the obligations (and client expectations) and the rules that need to be established to protect it. Who should have access to which libraries? What can be shared and what can’t be. How do you work with external partners and protect your content?
We can document your data policy, prepare your data privacy policies, incident response plans and data management structures, and we can set up compliance regular reporting.
We’ll implement the policies in your 365 and manage your data to make sure it’s where it should be, not suffering from duplication confusion or unintended leakage
Data Management
The tidier your data, the easier it is for AI to use it well to accelerate your productivity
Don’t wait until after you’ve been attacked
Get in touch to find out how kinetics KARE can protect your organisation
Download our latest executive “10 minute” briefing to share with colleagues

Read some of the latest news on Cyber-Security
Pretending to be you or your colleagues
Just because it seems safe, doesn't mean it is. On some emails, you might see a warning that marks them as being ‘external’. This gets added as the email comes into your organisation. The idea is a simple one – if you see an email marked as external, then you will be...
Avoiding ad trackers when you browse the ‘net
Your own personalised stalker It always seemed slightly creepy that your computer shows advertising that is strangely accurately targeted at things you might have been interested in. On the surface, that seems quite useful. If you have to tolerate ads on your...
Phishing emails are getting smarter every day
In the old days (ie last year!!), a dodgy email had a whiff to it – there was something that triggered your subconscious. That’s because some phishing emails were really badly written with terrible English. But others just had a sniff about them- something that made...
A cyber-criminal only needs to get lucky once. You have to stay ahead of them all day, every day
"A cybercriminal only has to be lucky once, while a defender has to be lucky every minute of every day.” - Combating Ransomware - A Comprehensive Framework for Action: Key Recommendations from the Ransomware Task Force. The message we hear from governance boards over...
Do you know where all your organisations data is? You don’t know what you don’t know
What is 'Shadow IT'? Shadow IT refers to the various web tools informally in use within most organisations. These tools are often chosen without reference to IT or to management in general. They are often used for all the very best reasons. Your colleagues have work...
Bad news email attachments
Some emails are more than just bad news No one likes bad news! But sometimes it can’t be helped. Sometimes it sneaks up on you. One of the most common ransomware attacks is through a compromised attachment in an email. It’s easy to say “only open stuff you expect” but...
When you willingly share data, how do you stop it leaking?
Data Leak Protection (DLP) is the name of several policies in Office 365, setting up what data can, and can't be, shared and with whom. Imagine being able to automatically identify private information like passport numbers, Health IDs or bank account details and make...
Newsflash – US Nuclear secrets leaked online through Shadow IT
This sounds like a nightmare that could never happen. US soldiers have been putting sensitive information online in non-secure third party websites. It defies belief, yet we’re reading that it happened. The story popped up on ‘Gizmodo’ . It is alleged that US Soldiers...
“LOCK ‘EM UP AND THROW AWAY THE KEYS”
Password Vaults and You With more and more websites necessary for our everyday activities, it’s getting harder and harder to manage passwords. By now, you will know not to write passwords on post-it notes and paste them on your screen. It's not uncommon for...
Google Releases Security Updates
Chrome security fixes Google has released Chrome version 91.0.4472.101 for Windows, Mac, and Linux. This update includes 14 security fixes. Out of the 14 fixes, 1 is considered to be critical in nature. If you are supported by KARE Core Fundamentals or Premium KARE...