
by Andrew Hunt | Nov 24, 2023 | News, Security
Imagine – you are busily going about your day when suddenly your meeting is interrupted. “No one can access their files!!!” or “We just accidently paid $50,000 to a fraudulent account and we can’t get it reversed!!!” or something similar. What would you do? Where...

by Andrew Hunt | Nov 24, 2023 | News, Security
We need to make some security changes. These are in accordance with the continued work by Microsoft to protect 365 users. This will keep your configuration current with their latest advisories but may have some (limited) impact on your IT experience. It is all about...

by Andrew Hunt | Nov 3, 2023 | News, Security
There is no silver bullet in cyber-security. Best practice requires layers of protection. One of those layers is ‘geo-blocking’, which means you can only log in from specified countries and overcomes many of the African and Eastern European hacker fraternities....

by Andrew Hunt | Oct 18, 2023 | News, Security
This is a great example of needing new tools that didn’t used to exist, to keep cyber-safe, even if they add cost to our cyber-protection. Hijacking your trust in LinkedIn Cybersecurity firm Cofense have detected phishing campaigns that used LinkedIn links...
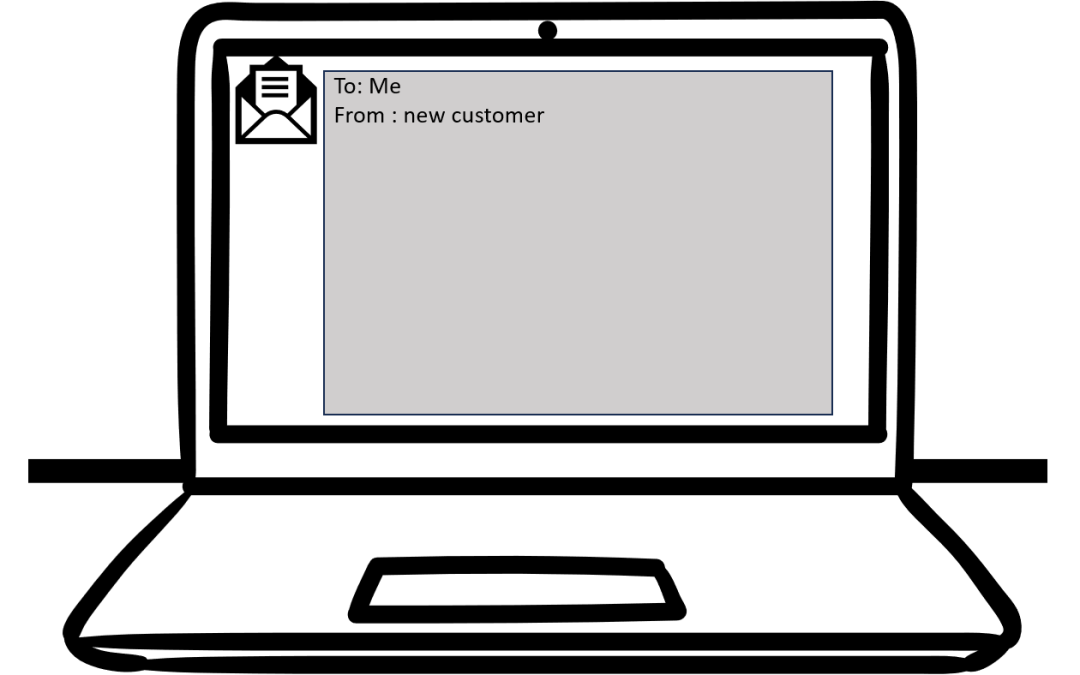
by Andrew Hunt | Oct 2, 2023 | News, Security
This is a real and very clever ‘spear-phishing’ attempt that one of our legal clients in Auckland received today. Would you have opened it? Would your IT have protected you? To: Me From : new customer Hello, My Husband and I are looking to buy a property...

by Andrew Hunt | Sep 29, 2023 | News, Security
News that an elderly woman was tricked out of $100,000 over Facebook won’t be a surprise to regular readers. She was fooled into thinking she was talking to a friend, and then sending money to access some make-believe Covid fund. AI makes it easy to speak in...








Recent Comments